One platform to manage them all
Secure all identities with ease in one place
Bots, APIs, service accounts, AI agents – your digital ecosystem runs on non-human identities. Without proper governance, they can become your weakest link. MidPoint brings visibility, control, and automation to every identity, whether human or machine.
Explore midPointbringing order to identity chaos
Gain visibility, enforce control, and automate at scale
Reduce risk from shadow IT
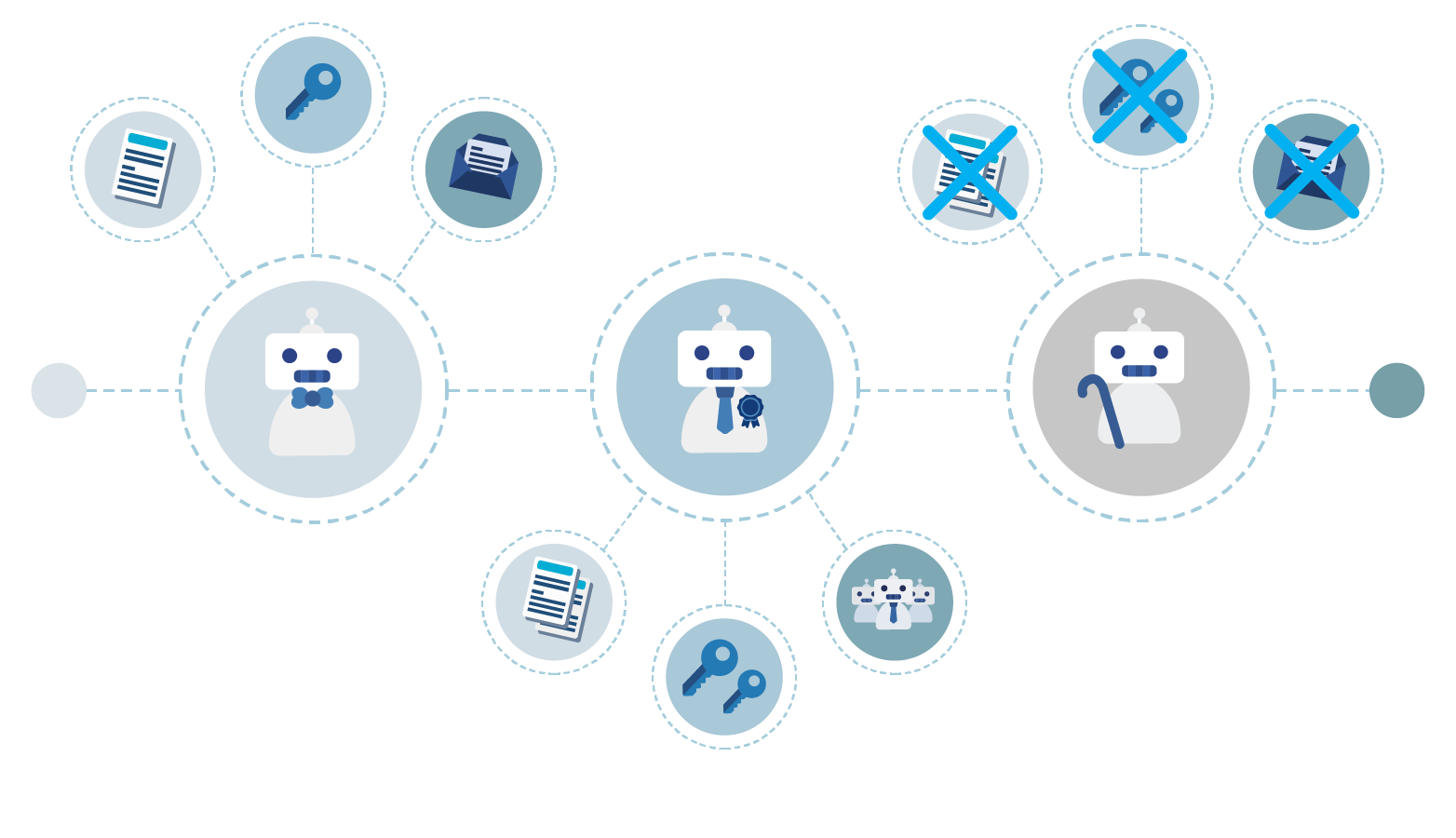
Discover, catalog, and monitor every machine identity across your entire infrastructure. Assign ownership to ensure proper lifecycle management so unmanaged machine identities can be detected and retired before they create security gaps.
See all your identities in one place
Get a complete overview of every identity, human or machine, along with its roles, entitlements, and relationships. Track dependencies, understand ownership, and prevent identity sprawl, all in one place with no add-ons required.
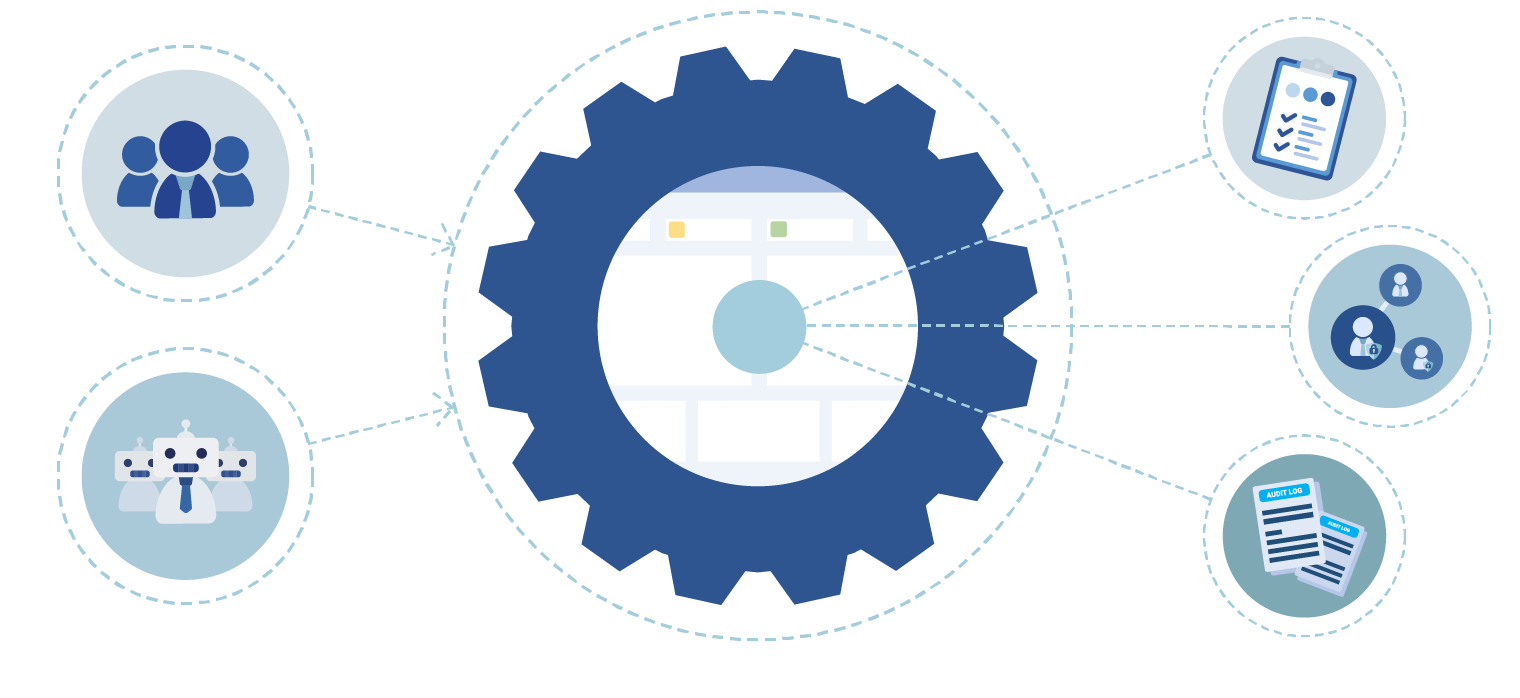
Automate governance
Continuously enforce policies like access control, approval chains, and access certifications. Ensure violations are reported, or trigger automated remediation processes, so compliance happens by design, not by last-minute audits. Custom dashboards and reports provide real-time insights into the state of governance across your environment.
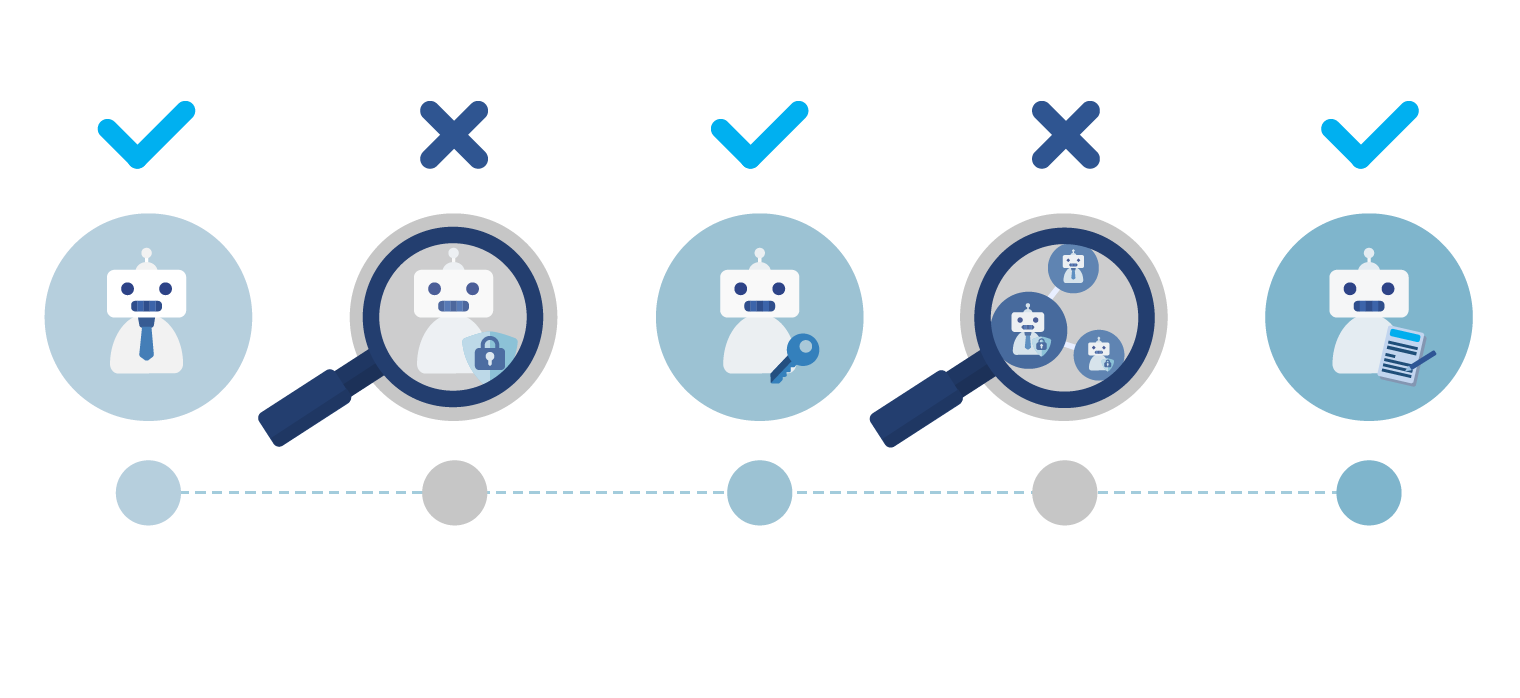
Implement Zero Trust security
MidPoint applies Zero Trust principles to every identity type. Each non-human identity gets only the access it needs, when it needs it, and nothing more. Least privilege is enforced automatically, ensuring machine identities cannot accumulate excessive rights.
Streamline operations
Automate the NHI lifecycle from end to end. Provisioning, updating, and removing NHIs no longer require manual intervention. MidPoint uses the same workflow principles as for users, reducing effort and human error while accelerating application rollouts and decommissioning.
the foundation of identity security
Accountability, automation, and compliance for every identity
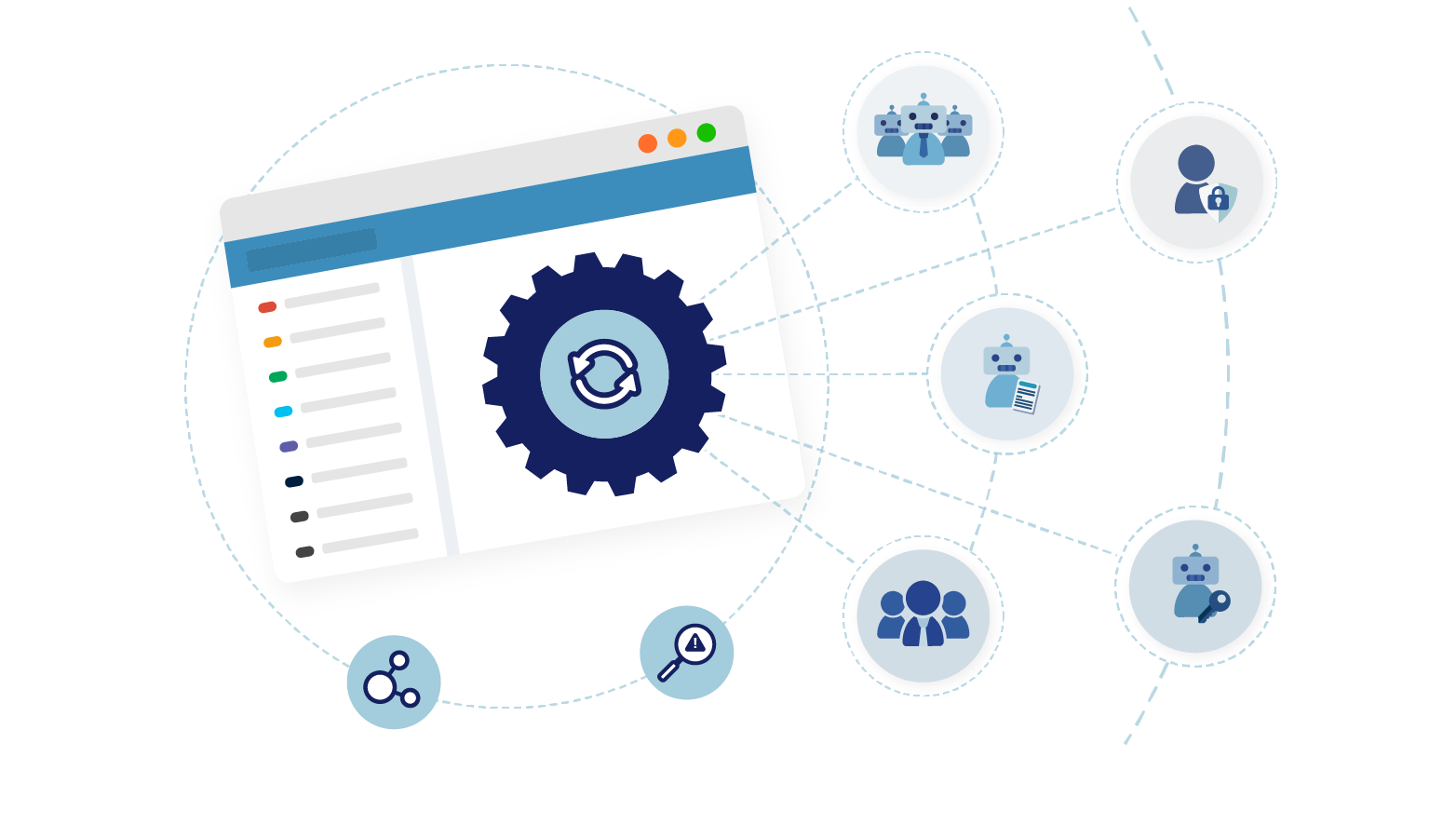
Full identity lifecycle management
Provision new service accounts with proper role assignments, update permissions through workflows, certify access during regular review cycles, and automatically decommission accounts when applications are retired. Each machine identity follows your organization’s joiner-mover-leaver process, eliminating forgotten service accounts that create security vulnerabilities and compliance gaps. Lifecycle policies also take into account the human owner dependency: for example, if the responsible person leaves, midPoint can trigger actions to reassign or retire the related machine identity.