Go with the best
MidPoint: the open source leader in identity security
Download midPoint Read technical documentationDrive your digital transformation with a system you can trust. Whether you prefer having it in the cloud, on-premise, or making use of both, when it comes to identity management and process efficiency, one should make no compromises. Go with the best by choosing the leading open source identity governance and administration platform midPoint.
Use midPoint’s excellent integration capabilities to connect as many source and target systems as you need and watch the synchronization magic happen. Enjoy up to date centralized data as well as organizational rules and policies that will empower you to be in control of identity and accesses it has. Experience true digital identity security with the freedom only open source software can give you. With no vendor lock-in or license fees. Unconditionally.
Make a difference
What you get with midPoint
Designed with pragmatism in mind, midPoint provides the following advanced features covering the technological and business identity needs of organizations.

2 million+
lines of thoroughly written code18 million
managed identities in one deployment100 million
identities scalability power
identity security
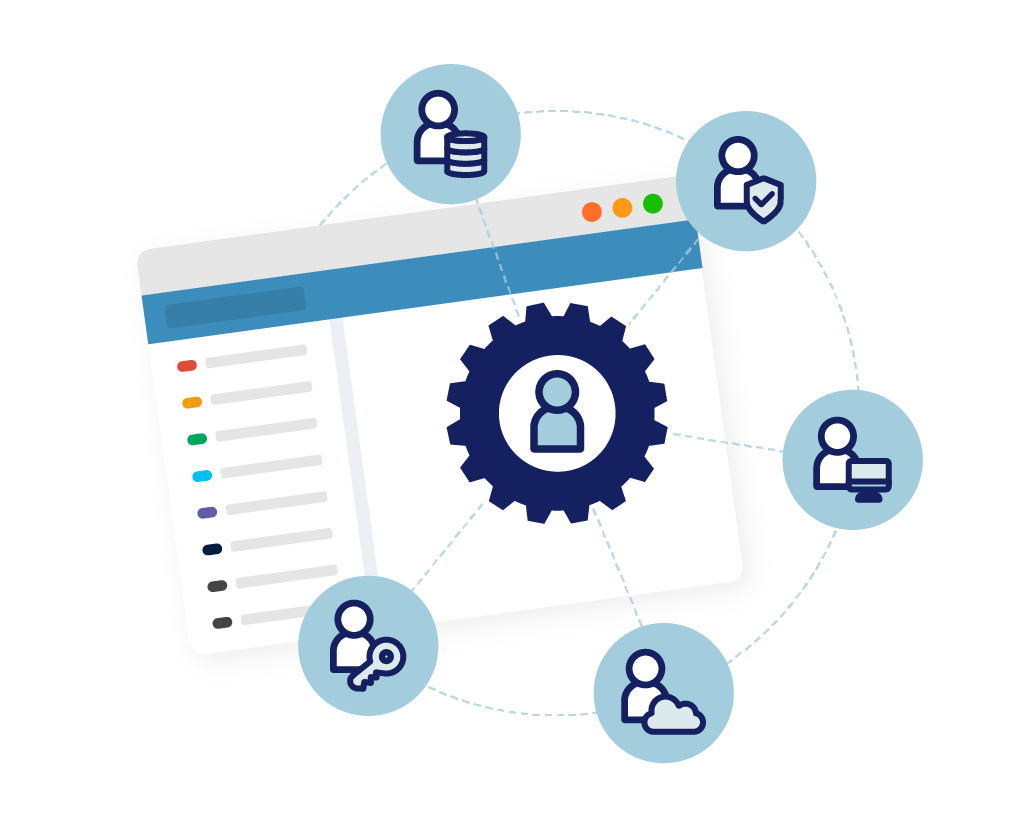
Highly Scalable Identity Governance and Administration
Make sure your identity data is consistent and up-to-date by using midPoint’s advanced synchronization possibilities. Be in control of who can access what and why, and have an overview of it in a single place. Speed up your identity processes with automated access requests. Magnify the IGA benefits with midScale enhancement as your organization grows, and handle deployments even with tens of millions of identities. MidPoint’s IGA also covers:
Confident decision making
Simulations
Avoid unnecessary risks safely and conveniently with simulations. Enjoy the possibility of using production data to see the impact of system changes before their implementation with no fear of crippling the system, as the changes are not permanent. Simulations will help you:
Predict the future
See beforehand what will happen during reconciliation.
Avoid unnecessary damage
Incorrect configuration can be fixed before changes are in effect.
See and analyze the quality of data
Leverage an interactive way of reporting and marking discrepancies.
Better understand the context
Recognize the exceptions in processes, rules, and policies.
Do the final testing in production without fear
During simulations, no changes are executed. They are only stored for later analysis.
from complex to simple
Identity Analytics
Simplify access management and enhance security and integrity of your system with artificial intelligence (AI) algorithms and analytical techniques designed to identify and address potential vulnerabilities and misconfigurations. Shift from a chaotic role permission model to a more organized business role-based model. Identity analytics includes:
overview and optimization
License Management
Use midPoint to manage the 3rd party software licenses of each user. Integrate midPoint with access management to minimize the amount of licenses in use with just-in-time provisioning. Get the most out of it with governance features:
Segregation
Prevent incompatible licenses being assigned to users.
Notifications
Learn when the number of used licenses approaches the maximum.
Monitoring
Avoid using more licenses than were purchased.
Life cycle
Use re-certification campaigns and time or activity based expiration to remove unused licenses.
Approval process
Enable user self-service requests controlled by defined approval processes.
Reporting
Stay informed about license usage.

visibility and accountability
Addressing Regulations and Compliance
Comply with regulations and govern data protection with the identity data visibility and accountability midPoint brings. Keep records of the lawful bases for data processing and enhance privacy by putting users in control of the flow and usage of their data. MidPoint covers:
power to the people
User Self-Service
Put the user in the driver’s seat and make their digital experience a ride they will surely enjoy. MidPoint’s user self-service will make the work process smoother by enabling:
-
-
-
Profile Management
-
connect them all
Multiple Identity Synchronization With Smart Correlation
Match digital user identities in a flexible and smart way. Use fuzzy search methods and weighted correlation rules to find matches even in noisy data across all systems. Connect as many as you want!
find out more
Get familiar with midPoint even further
Learn more information about midPoint and find out what latest midPoint release brings by means of the datasheet. Or give midPoint a go right away!
Professional open source
Download midPoint for free, test if before adoption, and enjoy its publicly available documentation. If you find yourself in need of professional support, we’ve got your back with our paid services.Partner presence in 45+ countries
Integrate midPoint with assistance from the partner of your choice. Engage Evolveum as well and get the most from the synergy of partner services and Evolveum’s support.Here for you since 2011
Go with the tried and trusted IGA platform used by small and big organizations alike all around the world, many of whom have been with us for more than a decade.Zero Trust without compromises
Adopt a Zero Trust approach to accelerate the security of your organization. Go for digital transformation to be efficiently in full control of the identity data.Worldwide community on hand
Join midPoint’s vivid global community, share and gain knowledge, and take part in making midPoint the best open source Identity Governance and Administration choice of tomorrow.No license fee software
Count with no initial costs affecting your project feasibility. MidPoint comes with zero licenses and a professional service pricing model adjustable to every organization.No vendor lock-in
Enjoy the benefits midPoint’s openness and freedom bring. Lift and shift independently, as the collaborative way midPoint is built avoids vendor lock-in.Legacy systems compatibility
Does your organization still use older technology to do the work? Use midPoint even with the legacy systems and enjoy the identity management and governance possibilities it brings.Cloud systems
Integrate midPoint with the cloud systems seamlessly and be in control over the identities conveniently from one place.
Logos shown are properties of their respective organizations.
Case studies
Learn about midPoint success
Read about challenges of organizations midPoint helped overcome. See how you can transform your identity struggle into identity success